Electronic Access Control System
New Version of Enterprise Access Control System
C•CURE 9000 Web Client lets you manage personnel, create reports, display dynamic views and monitor system activity anywhere in the world from your PC’s web browser.
Download C•CURE 9000 Version 2.9SP6. See How to Install the C•CURE Client.
You must be connected via VPN to access C•CURE 9000 Web Client and use your AD credentials (e.g., AD\username) to login. All users MUST connect to the C•CURE VPN Pool to access the C•CURE application or Web Client. See:
Purpose and Scope
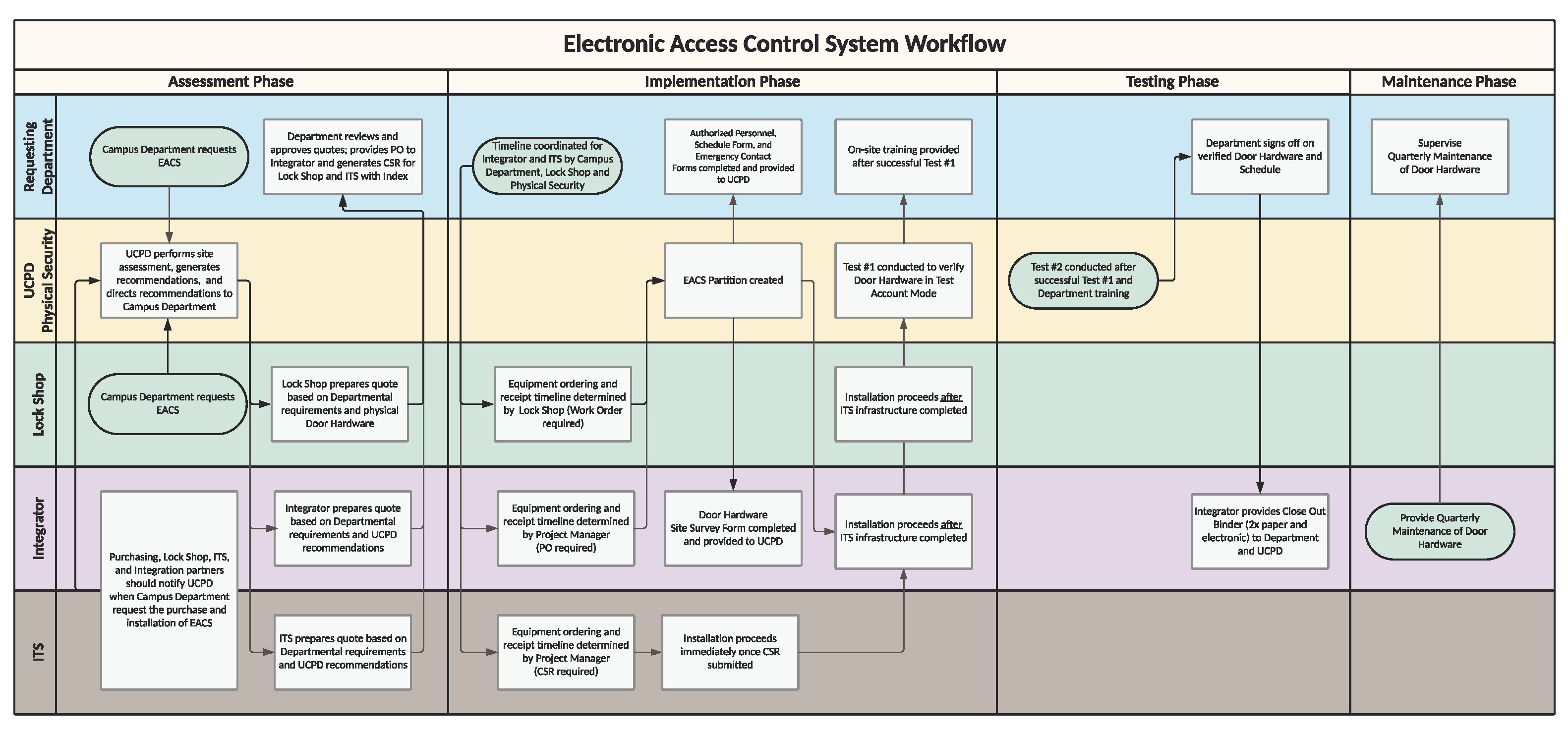
Effective physical and electronic security is essential in providing secure access, protecting people and assets, and mitigating natural or human threats or hazards. The scope of the keyless access upgrade project is to provide increased security and public safety by deploying electronic access controls, door status monitoring/security systems and rekeying the perimeter access points of university buildings.
The UC San Diego Police Department (UCPD), Environment, Health & Safety, and Facilities Management seek to maintain a safe campus environment for students, faculty, staff and visitors. These departments work collaboratively with community members to meet university access requirements for keys and electronic access control systems and to promptly address unauthorized use of devices to gain entry to university facilities and/or failure of individuals to safeguard keys at all times.
Depending on building or facility design and layout, access points will operate in the following manner:
- Designated entry doors will be locked and unlocked electronically, according to a predetermined schedule and will be accessible by card reader and/or PIN entry after hours and on weekends. In some cases, card reader and/or PIN entry may be required at all times for access to secure spaces, such as laboratories, storage locations, and other designated locations that require higher levels of security.
- Secondary perimeter doors will be locked and unlocked according to a schedule but will not be equipped with card readers.
- Egress only doors will remain secured at all times. These doors may also be equipped with a local sounder or piezo device that will alarm when they are propped or left open.
- All perimeter doors will be equipped with door status contacts and dog-down devices will be removed after rekeying.
After-hours building access is granted by presenting valid access credentials and/or PIN to create an audit trail. Building entrance doors will be rekeyed off building master keys to reduce the liability of lost or stolen keys. Emergency override keys will be issued to authorized building emergency responders only. Designated entry doors will be locked and unlocked electronically, according to established schedules.
An electronic access control system:
- Allows faculty, students, and staff to access buildings without mechanical keys
- Facilitates easy addition/removal of access to multiple buildings
- Reduces extended liability of stolen or lost building entrance keys
- Establishes an audit trail to document activity at each door
- Easy adjustment of perimeter door lock and unlock schedules
- Notifies campus police and departments if entry doors are forced open, held open, or malfunctioning
- Allows remote locking of perimeter doors on a building or group of buildings in the event of an emergency or active threat situation
UC San Diego’s enterprise-wide electronic access control system consists of an access control database and redundant, failover servers located in the ITS Data Center; access control hardware (card readers) installed in individual buildings; and individual departments will manage card/fob/PIN distribution. The centrally administered system allows the enterprise system administrators to grant system rights to Administrative Authorities as needed. Departments only have system administrator rights for buildings or areas for which the department has responsibility.
- Department Administrative Authorities, working in conjunction with the facility supervisors, are responsible to designate two individuals facility or department areas to act as primary and secondary Department Access Coordinators (DAC). Departments may assign additional DACs, depending on their specific requirements.
- The Administrative Authority may serve as the primary DAC, or delegate other individuals in the building to serve as primary or secondary DACs. The DAC will work with the Designated Security Integrator in maintaining the department’s access control and physical security systems program. Failure to designate a back-up DAC could delay processing of access transactions when the primary DAC is unavailable.
- Departments are responsible for controlling electronic card reader and/or PIN access to building entry and perimeter doors and to all areas assigned to, or under, the department’s control and responsibility.
- The department authorizing access for an individual is responsible for removing, returning, or revoking the access as required. This includes any metal keys or electronic access devices issued to allow access to department controlled areas. (See PPM 530-6 University Key Control)
- Keyless access installed on exterior building doors: Departments are responsible for all costs related to exterior door keyless access component installation, repair, and replacement in those areas where:
- Existing keyless access is not already in place and they have identified a departmental need or requirement
- Replacing standalone keyless entry systems that are not already integrated or capable of integrating with the existing enterprise-wide access control system
- State, federal, or university policies and/or regulations require keyless or enhanced access control to a building or area
- Keyless access installed on interior building doors: Departments are responsible for all costs related to interior door keyless access component installation, repair, and replacement. This includes any interior door keyless access installations performed after the original building construction.
Department Access Coordinators (DAC) are responsible for:
- Managing electronic card reader and/or PIN access to building entry and perimeter doors and other card access areas under the department’s control
- Granting or removing card reader authorization for user access to building entrances and other areas under the department’s control, including granting and removing access for new employees, departmentally sponsored visitors, retiring employees, terminated employees, and rotating student access as required
- Routinely contacting the Designated Security Integrator to re-authorize individual card-reader access users, based on the level of access and security required (The DAC should authorize the minimal level of access required for an individual to perform their assigned duties or responsibilities.)
- Terminating any means of electronic access to building perimeters or other university areas under their control when the user or employee leaves the department or university
- Maintaining accurate records for individuals who have been granted electronic access to building perimeter doors and all other areas under the department’s control
- Maintaining the electronic access control system and supported software documentation
Programming
- The Authorized Electronic Access Control System Integrator, herein referred to as Integrator, shall program all devices in accordance with the nomenclature and standards provided by the UCPD to ensure they are consistent with existing devices in the enterprise electronic access control system.
- Before the installation and activation of any IP addressable device for the electronic access control system, the Integrator shall provide:
- Hardware MAC address of IP addressable devices
- Make and model of the devices to be installed
- Building room number where the hardware will be installed
- Completed Electronic Access Control System
- Questionnaire
- Site Survey
The DAC and UC San Diego Police will coordinate the registration and firewall rule implementation of devices.
Startup and Commissioning
- The Integrator shall test each electronic access control system device in the presence of the DAC. Testing shall include placing the door in the controlled mode, using a valid card and/or PIN to release the door, using the request-to-exit device (if installed) to release the door, and placing the door back in the unlocked state.
- The Integrator shall test each door alarm function, including door forced open, door held open, device tamper, AC-power loss, and low battery.
- The Integrator shall conduct a test to verify that the local card reader and/or PIN device authorized user database and door schedule is stored locally on the card reader and panel to ensure functionality in the event of network loss or connectivity to the electronic access control system server.
- The Integrator shall conduct a test to ensure that the door is either in a “Fail Safe” (unlocked) or “Fail Secure” (locked) state, as appropriately identified by the DAC and UCPD, upon loss of power to the panel and/or card reader. If uninterrupted access is required for the building, area, or room, coordination for a UPS backup or power-generator outlet shall be included in the scope of work as needed.
- The DAC and UCPD will conduct field audits for installations to verify adherence to these design standards, including appropriate wiring practices for the devices.
- The electronic access control system warranty shall begin upon completion of the field audit and university acceptance of the installation.
- In coordination with the DAC and UCPD, the Integrator shall coordinate the installation of system software to preauthorized departmental DAC workstations.
- The Integrator shall:
- Provide a minimum of four hours of onsite training in coordination with the department designated DACs.
- Troubleshoot and resolve device-related problems.
- Coordinate and automate the notification of device-related problems to the DACs.
- Perform firmware upgrades as required
The UCPD Physical Security Program designee will:
- Ensure that the electronic access control system server is online and functioning.
- Validate the redundant, failover system server is functioning and tested quarterly.
- Request and ensure proper backup and system firewall templates are applied and maintained.
- Maintain system records, including purging transactions every 12 months to maintain system performance.
- Coordinate system-related activities between the Integrator, ITS, and DACs as appropriate to ensure successful device installation.
- Troubleshoot and resolve system-related problems.
- Actively audit system account management.
- Document and submit change management requests for proper approval as required for any change that may affect system-wide end users and departments.
- Schedule and perform system-level housekeeping and audit activities to ensure optimal system operation.
- Coordinate and confirm system Backups.
- Request firewall configuration for devices, authorized DAC workstations, and integration with Milestone XProtect Video Management System as necessary.
- Coordinate and automate the notification of system-related problems to the DACs.
- Install security patches, upgrade software packages, and update the system configuration to meet university and industry best practices.
- Maintain operating system and supported software documentation.
|
Service
|
Client
|
UCPD
|
|
Maintain client/user contact information
|
X
|
|
|
Maintain DAC contact information
|
|
X
|
|
Approve all hardware and software installation
|
X
|
X
|
|
Coordinate with Integrators to resolve device problems
|
X
|
|
|
Coordinate with Integrators to resolve system problems
|
|
X
|
|
Propose hardware/software configuration and installation standards
|
|
X
|
Click image to view larger a version.
Questions?
Contact Renato Nerida, (858) 246-3069.